
New "DoubleClickjacking" Exploit Bypasses Clickjacking Protections on Major Websites
A new “widespread timing-based vulnerability class” that uses a double-click sequence to enable clickjacking attacks and account takeovers on practically all popular websites has been revealed by threat hunters.
DoubleClickjacking is the codename given by security researcher Paulos Yibelo to the technique.
“Instead of relying on a single click, it takes advantage of a double-click sequence,” Yibelo claimed. “While it might sound like a small change, it opens the door to new UI manipulation attacks that bypass all known clickjacking protections, including the X-Frame-Options header or a SameSite: Lax/Strict cookie.”
What is DoubleClickjacking?
DoubleClickjacking is a new, sneaky way that hackers can trick users into doing something they didn’t mean to, like authorizing an attack on their account, all by taking advantage of the timing between two clicks in a double-click. It’s similar to an older attack called clickjacking, but this one is much harder to defend against because it doesn’t rely on the usual protections websites use.
How Does DoubleClickjacking Work?
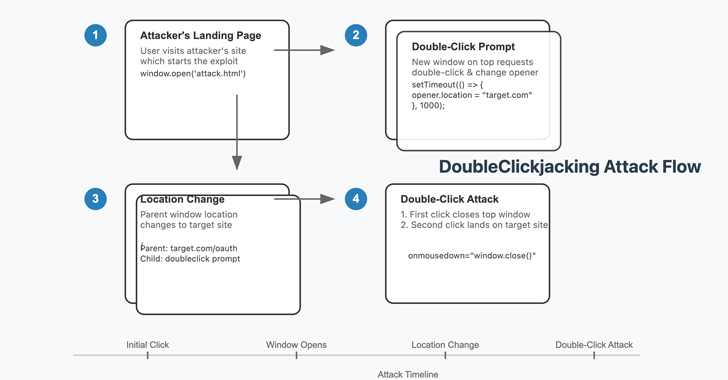
Here’s how the attack unfolds:
- The Attack Begins:
- The attacker lures the victim to their website. The attacker’s page could open a new tab or window, perhaps looking like something harmless, like a captcha or a simple verification step.
- The Double-Click Trick:
- The victim is prompted to double-click to complete the action. While they’re doing that, the attacker’s site secretly redirects the victim’s parent window (the original page they were on) to a malicious page. This could be a page asking the victim to authorize a harmful action, like allowing an attacker to access their account.
- Confirmation Hijacking:
- As the victim is focused on the double-click action, they might not notice that the attacker’s page has closed the original window. The victim might then be presented with a permission dialog on the parent website, which they unknowingly approve, giving the attacker access to their account or sensitive data.
Why is This Dangerous?
The problem with DoubleClickjacking is that it’s sneaky and quick, and it bypasses many of the usual defenses websites use to protect against clickjacking attacks.
Normally, websites use things like X-Frame-Options (which stops sites from embedding their pages inside iframes) or SameSite cookies (to protect against cross-site attacks). But DoubleClickjacking doesn’t need those—it takes advantage of the tiny gap between the two clicks in a double-click. And because this type of manipulation wasn’t anticipated in older defenses, many websites are left vulnerable.
Real-World Impact
Imagine this happening on a site like Yahoo or Coinbase. These sites use OAuth for logging in and authorizing apps. DoubleClickjacking could trick someone into approving a malicious OAuth application, giving the attacker full access to their account without the user realizing it.
This kind of attack could result in account takeovers and data theft. Since the attack doesn’t require the user to do much other than double-click, it’s easy for hackers to pull off without being noticed.
How Can Websites Protect Against This?
- Client-Side Protection:
- Websites can stop this by making sure critical buttons (like “submit” or “approve”) are inactive by default. They should only become active after the user does something intentional, like making a specific mouse gesture or pressing a key.
- Stronger Browser Defenses:
- Browser makers can help by adding new standards to prevent this kind of timing manipulation. This would be similar to how X-Frame-Options prevents clickjacking from iframes.
- Be Careful with Double-Clicking:
- Websites should make sure that double-clicking doesn’t automatically trigger important actions. Adding an extra confirmation step, like asking if you really want to submit or approve something, can help stop the attack.
- User Awareness:
- Users should be careful when they’re interacting with unfamiliar websites. If something seems fishy, like double-clicking to approve something or strange popups, it’s always a good idea to pause and double-check.
As long-term solutions, it’s recommended that browser vendors adopt new standards akin to X-Frame-Options to defend against double-click exploitation.
“DoubleClickjacking is a twist on a well-known attack class,” Yibelo said. “By exploiting the event timing between clicks, attackers can seamlessly swap out benign UI elements for sensitive ones in the blink of an eye.”
The revelation comes almost a year after the researcher also showed off cross window forgery, also known as gesture-jacking, another type of clickjacking that involves tricking a victim into pressing or holding down the Enter key or Space bar on a website under the control of an attacker in order to start a malicious action.
The ability to take over an account on websites such as Yahoo! and Coinbase might be used “if a victim that is logged into either site goes to an attacker website and holds the Enter/Space key.”
“This is possible because both sites allow a potential attacker to create an OAuth application with wide scope to access their API, and they both set a static and / or predictable ‘ID’ value to the ‘Allow/Authorize’ button that is used to authorize the application into the victim’s account.”
