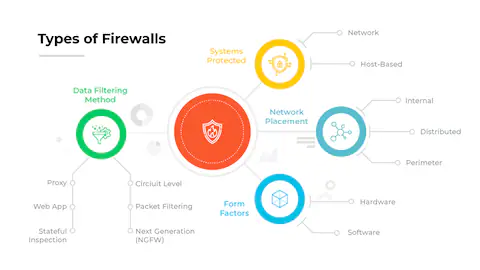
Different Types of Network Firewalls
The tools used to stop illegal access to private networks are called network firewalls. A firewall, which can be either software or hardware, is a security solution for computers or other devices that are linked to a network. Incoming and outgoing traffic, or the volume of data flowing over a computer network at any given …
READ MORE